TECH
Revolutionizing Industries: Exploring Blockchain Applications and Their Impact
From enabling secure financial transactions to authenticating the origin of physical and digital goods, blockchain technology...
By Robert BrownJuly 4, 20234 Effective Strategies for Promoting Employee Engagement To Improve Their Mental Health
Picture this: You walk into your office on a Monday morning, and the energy is electric....
By Robert BrownJuly 3, 2023Microsoft Office Professional Plus 2019: What Does It Include?
Users have all the tools they need to accomplish their tasks with the application. With Office...
By Robert BrownJuly 3, 2023Security Guard Management Software: Streamline Your Operations for Success
As a security guard manager, it can be challenging always to keep an eye on every...
By Robert BrownJune 29, 2023User-Centered Design: How to Build Mobile Apps that Delight Your Customers
Every user wants the mobile application to be intuitive, easy to access, and user-friendly. This is...
By Robert BrownJune 28, 2023How Does a Clinic Management Software Streamline Administrative Tasks?
Clinic management software is a powerful tool that streamlines administrative tasks and simplifies patient care. By...
By Robert BrownJune 28, 2023What Are the Benefits of Home Automation?
Before now, having to automate your home was not something that everyone thought was necessary. This...
By Robert BrownJune 28, 2023What Are the Applications of PEG?
PEG, or polyethylene glycol, is a synthetic material with countless applications in various industries. Mostly, it’s...
By Robert BrownJune 28, 2023How to Choose the Best VoIP System for Your Business Needs
Choosing the right VoIP system for your business needs starts with understanding your company’s needs. Afterward,...
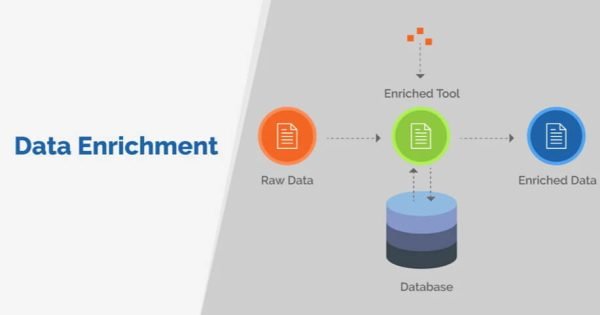
By Robert BrownJune 28, 20237 Best Data Enrichment Tools to Level Up Your Sales
Data enrichment is all about obtaining more information. But how do data enrichment tools work, and...
By Robert BrownJune 28, 2023Introducing XCN Coins-Revealing Its Key Features, Transaction Speed, And Security
Chain (XCN) is basically a well-established blockchain project that aims to enhance financial series for enterprises...
By Robert BrownJune 26, 20235 Things You Must Know About Generative Artificial Intelligence
Generative Artificial Intelligence has emerged as a revolutionary technology with the power to transform various industries....
By Robert BrownJune 24, 2023How to Read Text Messages from Another Phone without Them Knowing
Texting is arguably the most popular mode of communicating via cellular devices. Statistics show that 88%...
By Robert BrownJune 22, 2023Python Security Coding Practices
Python is a robust programming language for creating web apps, APIs, scripts, and other types of...
By Robert BrownJune 21, 2023Why virtualize your catalog in PDF format?
Since its initial launch in 1993, the main virtue of this type of file is to...
By Robert BrownJune 20, 2023You May Need:
Recent Posts
Categories
- AUTO279
- BUSINESS772
- CONSTRUCTION55
- CRYPTOCURRENCY18
- EDUCATION124
- ENTERTAINMENT375
- FAMILY & RELATIONSHIPS1
- FASHION129
- FEATURE5
- FINANCE159
- GIFT IDEAS2
- HEALTH363
- HOME IMPROVEMENT682
- LAW272
- LIFESTYLE396
- OUTDOOR58
- PACKAGING6
- Parenting & Children's Products1
- PET17
- REAL ESTATE128
- SEO DIGITAL22
- SPORTS1
- TECH233
- TRAVEL93
- Uncategorized6